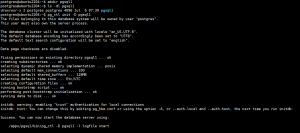
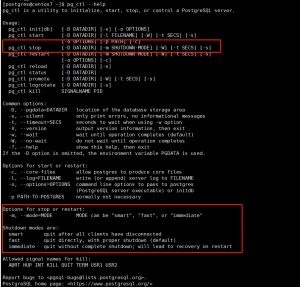
1、ssh服务介绍
ssh:secure shell protocol,端口:22/tcp, 安全的远程登录,实现加密通信,代替传统的 telnet 协议。
- 具体的软件实现:
- OpenSSH:ssh协议的开源实现,CentOS 默认安装
- dropbear:另一个ssh协议的开源项目的实现
- SSH 协议版本
- v1:基于CRC-32做MAC,不安全;man-in-middle
- v2:双方主机协议选择安全的MAC方式,基于DH算法做密钥交换,基于RSA或DSA实现身份认证
1.1、公钥交换原理
![图片[1]-ssh服务-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-81.png)
- 客户端发起链接请求;
- 服务端返回自己的公钥,以及一个会话ID(这一步客户端得到服务端公钥);
- 客户端生成密钥对;
- 客户端用自己的公钥异或会话ID,计算出一个值Res,并用服务端的公钥加密;
- 客户端发送加密后的值到服务端,服务端用私钥解密,得到Res;
- 服务端用解密后的值Res异或会话ID,计算出客户端的公钥(这一步服务端得到客户端公钥);
- 最终:双方各自持有三个秘钥,分别为自己的一对公、私钥,以及对方的公钥,之后的所有通讯都会被加密。
1.2、ssh加密通讯原理
![图片[2]-ssh服务-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-82.png)
2、openssh 服务
OpenSSH是SSH (Secure SHell) 协议的免费开源实现,一般在各种Linux版本中会默认安装,基于C/S结构。
Openssh软件相关包:
- openssh
- openssh-clients
- openssh-server
# openssh 相关包
[root@centos79 certs]# rpm -qa openssh*
openssh-clients-7.4p1-21.el7.x86_64
openssh-7.4p1-21.el7.x86_64
openssh-server-7.4p1-21.el7.x86_64
[root@centos79 certs]# rpm -ql openssh-server
/etc/pam.d/sshd
/etc/ssh/sshd_config
/etc/sysconfig/sshd
/usr/lib/systemd/system/sshd-keygen.service
/usr/lib/systemd/system/sshd.service
/usr/lib/systemd/system/sshd.socket
/usr/lib/systemd/system/sshd@.service
/usr/lib64/fipscheck/sshd.hmac
/usr/libexec/openssh/sftp-server
/usr/sbin/sshd
/usr/sbin/sshd-keygen
/usr/share/man/man5/moduli.5.gz
/usr/share/man/man5/sshd_config.5.gz
/usr/share/man/man8/sftp-server.8.gz
/usr/share/man/man8/sshd.8.gz
/var/empty/sshd
[root@centos79 certs]# rpm -ql openssh-clients
/etc/ssh/ssh_config
/usr/bin/scp
/usr/bin/sftp
/usr/bin/slogin
/usr/bin/ssh
/usr/bin/ssh-add
/usr/bin/ssh-agent
/usr/bin/ssh-copy-id
/usr/bin/ssh-keyscan
/usr/lib64/fipscheck/ssh.hmac
/usr/libexec/openssh/ssh-pkcs11-helper
/usr/share/man/man1/scp.1.gz
/usr/share/man/man1/sftp.1.gz
/usr/share/man/man1/slogin.1.gz
/usr/share/man/man1/ssh-add.1.gz
/usr/share/man/man1/ssh-agent.1.gz
/usr/share/man/man1/ssh-copy-id.1.gz
/usr/share/man/man1/ssh-keyscan.1.gz
/usr/share/man/man1/ssh.1.gz
/usr/share/man/man5/ssh_config.5.gz
/usr/share/man/man8/ssh-pkcs11-helper.8.gz
[root@centos79 certs]# rpm -ql openssh
/etc/ssh
/etc/ssh/moduli
/usr/bin/ssh-keygen
/usr/libexec/openssh
/usr/libexec/openssh/ctr-cavstest
/usr/libexec/openssh/ssh-keysign
/usr/share/doc/openssh-7.4p1
/usr/share/doc/openssh-7.4p1/CREDITS
/usr/share/doc/openssh-7.4p1/ChangeLog
/usr/share/doc/openssh-7.4p1/INSTALL
/usr/share/doc/openssh-7.4p1/OVERVIEW
/usr/share/doc/openssh-7.4p1/PROTOCOL
/usr/share/doc/openssh-7.4p1/PROTOCOL.agent
/usr/share/doc/openssh-7.4p1/PROTOCOL.certkeys
/usr/share/doc/openssh-7.4p1/PROTOCOL.chacha20poly1305
/usr/share/doc/openssh-7.4p1/PROTOCOL.key
/usr/share/doc/openssh-7.4p1/PROTOCOL.krl
/usr/share/doc/openssh-7.4p1/PROTOCOL.mux
/usr/share/doc/openssh-7.4p1/README
/usr/share/doc/openssh-7.4p1/README.dns
/usr/share/doc/openssh-7.4p1/README.platform
/usr/share/doc/openssh-7.4p1/README.privsep
/usr/share/doc/openssh-7.4p1/README.tun
/usr/share/doc/openssh-7.4p1/TODO
/usr/share/licenses/openssh-7.4p1
/usr/share/licenses/openssh-7.4p1/LICENCE
/usr/share/man/man1/ssh-keygen.1.gz
/usr/share/man/man8/ssh-keysign.8.gz
- 服务器端程序
- /usr/sbin/sshd
- Unit 文件
- /usr/lib/systemd/system/sshd.service
- 客户端:
- Linux Client:ssh, scp, sftp,slogin
- Windows Client:xshell,MobaXterm,putty,securecrt,sshsecureshellclient
2.1、客户端 ssh命令
ssh命令是ssh客户端,允许实现对远程系统经验证地加密安全访问。
当用户远程连接ssh服务器时,会复制ssh服务器 /etc/ssh/ssh_host*key.pub 文件中的公钥到客户机的~/.ssh/know_hosts中。下次连接时,会自动匹配相对应的私钥,不能匹配,将拒绝连接。
ssh客户端配置文件: /etc/ssh/ssh_config
#StrictHostKeyChecking ask
#首次登录不显示检查提示
StrictHostKeyChecking no
# IdentityFile ~/.ssh/id_rsa
# IdentityFile ~/.ssh/id_dsa
# IdentityFile ~/.ssh/id_ecdsa
# IdentityFile ~/.ssh/id_ed25519
# Port 22# 格式
ssh [user@]host [COMMAND]
ssh [-l user] host [COMMAND]
# 选项
-p port #远程服务器监听的端口
-b #指定连接的源IP
-v #调试模式
-C #压缩方式
-X #支持x11转发
-t #强制伪tty分配,如:ssh -t remoteserver1 ssh -t remoteserver2
ssh remoteserver3
-o option 如:-o StrictHostKeyChecking=no
-i <file> #指定私钥文件路径,实现基于key验证,默认使用文件: ~/.ssh/id_dsa,
~/.ssh/id_ecdsa, ~/.ssh/id_ed25519,~/.ssh/id_rsa等
# 通过多个跳板登录远程主机192.168.1.1
ssh -t 192.168.1.2 -t 192.168.1.3 ssh 192.168.1.1
root@192.168.1.2's password:
root@192.168.1.3's password:
root@192.168.1.1's password:
Last login: Sun Nov 13 16:42:15 2022 from 192.168.1.3# 远程执行命令
[root@centos79-base01 ~]# ssh 192.168.1.11 pwd
Warning: Permanently added '192.168.1.11' (ECDSA) to the list of known hosts.
root@192.168.1.11's password:
/root
# 在远程主机运行本地shell脚本
[root@centos79-base01 ~]# cat test.sh
#!/bin/bash
hostname -I
[root@centos79-base01 ~]# ssh 192.168.1.11 /bin/bash < test.sh
root@192.168.1.11's password:
192.168.1.11# 统计ssh登录失败次数最多的前十个远程IP
lastb -f btmp-test | awk '{print $3}'|sort |uniq -c|sort -nr|head
lastb -f btmp-test | awk '{ip[$3]++}END{for(i in ip){print ip[i],i}}'|sort -nr|head# 利用windows 显示 Linux 的图形工具
#在windows 开启X Server的软件,如:Xmanager,观察的窗口的编号,如:0.0
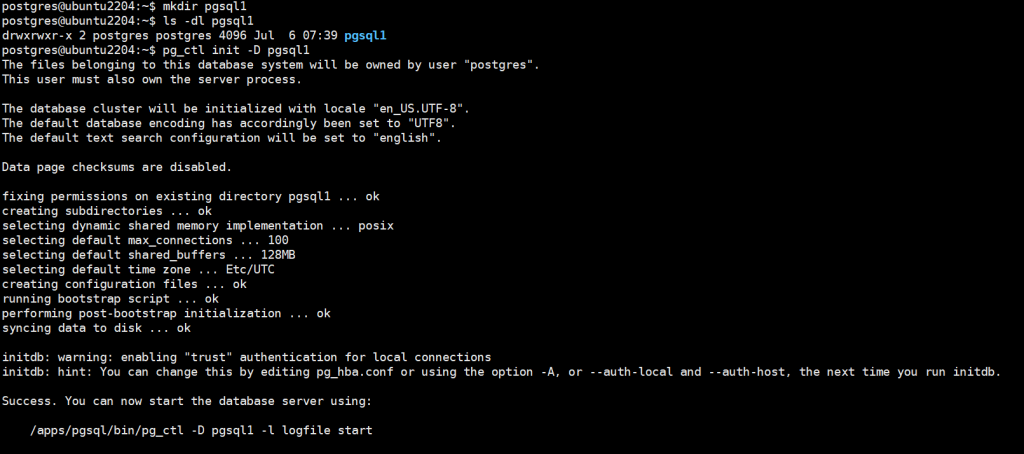
[root@centos79-base01 ~]# yum -y install firefox
[root@centos79-base01 ~]# export DISPLAY=192.168.1.1:0.0
[root@centos79-base01 ~]# firefox
![图片[3]-ssh服务-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-83.png)
![图片[4]-ssh服务-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-84.png)
2.2、其它ssh客户端工具
# scp命令
scp [options] SRC... DEST/
# 方式
scp [options] [user@]host:/sourcefile /destpath
scp [options] /sourcefile [user@]host:/destpath
scp [options] [user@]host1:/sourcetpath [user@]host2:/destpath
# 选项
-C 压缩数据流
-r 递归复制
-p 保持原文件的属性信息
-q 静默模式
-P PORT 指明remote host的监听的端口
# rsync命令
# rsync工具可以基于ssh和rsync协议实现高效率的远程系统之间复制文件,使用安全的shell连接做为传输方式,比scp更快,基于增量数据同步,即只复制两方不同的文件,此工具来自于rsync包。
# 通信两端主机都需要安装 rsync 软件
rsync -av /etc server1:/tmp/ #复制目录和目录下文件
rsync -av /etc/ server1:/tmp/ #只复制目录下文件
# 选项
-n 模拟复制过程
-v 显示详细过程
-r 递归复制目录树
-p 保留权限
-t 保留修改时间戳
-g 保留组信息
-o 保留所有者信息
-l 将软链接文件本身进行复制(默认)
-L 将软链接文件指向的文件复制
-u 如果接收者的文件比发送者的文件较新,将忽略同步
-z 压缩,节约网络带宽
-a 存档,相当于-rlptgoD,但不保留ACL(-A)和SELinux属性(-X)
--delete 源数据删除,目标数据也自动同步删除
--progress 显示进度
--bwlimit=5120 #限速以KB为单位,5120表示5MB
#范例
[root@centos79-base01 ~]# yum install -y rsync
[root@centos79-base01 ~]# rsync -auv --progress --delete /data/epel 192.168.1.11:/root
# sftp命令
# 交互式文件传输工具,用法和传统的ftp工具相似,利用ssh服务实现安全的文件上传和下载
# 使用ls cd mkdir rmdir pwd get put等指令或help获取帮助信息
sftp [user@]host
sftp> help
# 自动登录 ssh工具 sshpass
# ssh登陆不能在命令行中指定密码。sshpass的出现,解决了这一问题。sshpass用于非交互SSH的密码验证,一般用在sh脚本中,无须再次输入密码(本机known_hosts文件中有的主机才能生效)。它允许你用 -p 参数指定明文密码,然后直接登录远程服务器,它支持密码从命令行、文件、环境变量中读取。
sshpass [option] command parameters
# 选项
-p password #后跟密码它允许你用 -p 参数指定明文密码,然后直接登录远程服务器
-f filename #后跟保存密码的文件名,密码是文件内容的第一行
-e #将环境变量SSHPASS作为密码
# 范例
[root@centos79-base01 ~]# yum -y install sshpass
[root@centos79-base01 ~]# rpm -ql sshpass
/usr/bin/sshpass
/usr/share/doc/sshpass-1.06
/usr/share/doc/sshpass-1.06/AUTHORS
/usr/share/doc/sshpass-1.06/COPYING
/usr/share/doc/sshpass-1.06/ChangeLog
/usr/share/doc/sshpass-1.06/NEWS
/usr/share/man/man1/sshpass.1.gz
[root@centos79-base01 ~]# sshpass -p root123 ssh 192.168.1.11 hostname -I
192.168.1.11
# 批量修改多台主机的root密码为随机密码
#!/bin/bash
rpm -q sshpass &> /dev/null || yum -y install sshpass
export SSHPASS=root123
NET=192.168.1
for i in {1..254};do
{
PASS=`openssl rand -base64 9`
sshpass -e ssh -o StrictHostKeyChecking=no $NET.$i "echo $PASS|passwd --stdin root &> /dev/null"
echo $NET.$i:$PASS >> host.txt
}&
done
wait
# 批量部署多台主机基于key验证脚本1
#!/bin/bash
NET=192.168.1
PASS=root123
ssh-keygen -P "" -f /root/.ssh/id_rsa &> /dev/null
rpm -q sshpass &> /dev/null || yum -y install sshpass &> /dev/null
for i in {1..100};do
{
sshpass -p $PASS ssh-copy-id -o StrictHostKeyChecking=no -i /root/.ssh/id_rsa.pub $NET.$i &> /dev/null
}&
done
wait
# 批量部署多台主机基于key验证脚本2
#!/bin/bash
HOSTS="
192.168.1.1
192.168.1.2
192.168.1.3
"
PASS=root123
ssh-keygen -P "" -f /root/.ssh/id_rsa &> /dev/null
rpm -q sshpass &> /dev/null || yum -y install sshpass &> /dev/null
for i in $HOSTS;do
{
sshpass -p $PASS ssh-copy-id -o StrictHostKeyChecking=no -i
/root/.ssh/id_rsa.pub $i &> /dev/null
}&
done
wait
2.3、ssh登录验证方式介绍
- 用户/口令
- 基于密钥
![图片[5]-ssh服务-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-85.png)
- 客户端发起ssh请求,服务器会把自己的公钥发送给用户
- 用户会根据服务器发来的公钥对密码进行加密
- 加密后的信息回传给服务器,服务器用自己的私钥解密,如果密码正确,则用户登录成功
![图片[6]-ssh服务-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-86.png)
- 首先在客户端生成一对密钥(ssh-keygen)
- 并将客户端的公钥ssh-copy-id 拷贝到服务端
- 当客户端再次发送一个连接请求,包括ip、用户名
- 服务端得到客户端的请求后,会到authorized_keys中查找,如果有响应的IP和用户,就会随机生
成一个字符串,例如:root123 - 服务端将使用客户端拷贝过来的公钥进行加密,然后发送给客户端
- 得到服务端发来的消息后,客户端会使用私钥进行解密,然后将解密后的字符串发送给服务端
- 服务端接受到客户端发来的字符串后,跟之前的字符串进行对比,如果一致,就允许免密码登录
2.4、实现基于密钥的登录方式
# 在客户端生成密钥对
ssh-keygen -t rsa [-P 'password'] [-f “~/.ssh/id_rsa"]
# 把公钥文件传输至远程服务器对应用户的家目录
ssh-copy-id [-i [identity_file]] [user@]host
# 重设私钥口令
ssh-keygen -p
# 验证代理(authentication agent)保密解密后的密钥,口令就只需要输入一次,在GNOME中,代理被自动提供给root用户
#启用代理
ssh-agent bash
#钥匙通过命令添加给代理
ssh-add
# 在SecureCRT或Xshell实现基于key验证
# 在SecureCRT工具—>创建公钥—>生成Identity.pub文件
# 转化为openssh兼容格式(适合SecureCRT,Xshell不需要转化格式),并复制到需登录主机上相应文件authorized_keys中,注意权限必须为600,在需登录的ssh主机上执行
ssh-keygen -i -f Identity.pub >> .ssh/authorized_keys# 实现基于 key 验证
[root@centos79-base01 ~]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): #回车,接受默认值
Created directory '/root/.ssh'.
Enter passphrase (empty for no passphrase): #回车,接受默认值,空密码
Enter same passphrase again: #回车,接受默认值
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:T9imV0jc3otYPnQ5nCePQYljkbZTlWlSc41QyKM5iwc root@centos79-base01
The key's randomart image is:
+---[RSA 2048]----+
| .o=o=*|
| . .*+o=+|
| o+=+= |
| E+++o= o |
| So=o=.X .|
| .=o* o O |
| ..+ + o .|
| . . |
| |
+----[SHA256]-----+
[root@centos79-base01 ~]# ll .ssh/
total 8
-rw------- 1 root root 1679 Nov 13 17:43 id_rsa
-rw-r--r-- 1 root root 402 Nov 13 17:43 id_rsa.pub
[root@centos79-base01 ~]# cat .ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDCfkeZGVjaFApoRP2tFcFSAnkXRGJGY9lYqUrVLmy8htlCn/BLuK7T4gLCHRkDqWKmeVRP94D3A2fe+dzO3OT9pNqpUdtNp6tEQcTArUEy4IIVIufO41dfLgYVNR2d3T1Yd9Yy4PAJSJItbHlWGfAkr7iCVsp6EDsbMKuFe+uhYrDzSIG75adfjCz+bJBtbHimVIWrnQ5819z2+CV70hqooNPBnBM2z6/UNoObA/pRxZ4g9huS8GuuYen5Gif0nB5jW+msOaTDEXXgjndf0AIr1FoXbcEEi9YnZW78YFSGNWausoe+SM6C0S75unn/BDLhTsQUSHhc3/+JJ5hqVBHl root@centos79-base01
[root@centos79-base01 ~]# cat .ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAwn5HmRlY2hQKaET9rRXBUgJ5F0RiRmPZWKlK1S5svIbZQp/w
S7iu0+ICwh0ZA6lipnlUT/eA9wNn3vncztzk/aTaqVHbTaerREHEwK1BMuCCFSLn
zuNXXy4GFTUdnd09WHfWMuDwCUiSLWx5VhnwJK+4glbKehA7GzCrhXvroWKw80iB
u+WnX4ws/myQbWx4plSFq50OfNfc9vgle9IaqKDTwZwTNs+v1DaDmwP6UcWeIPYb
kvBrrmHp+Ron9JweY1vprDmkwxF14I53X9ACK9RaF23BBIvWJ2Vu/GBUhjVmrrKH
vkjOgtEu+bp5/wQy4U7EFEh4XN//iSeYalQR5QIDAQABAoIBABQu6J0xrS/MXpwd
dLnOhSZOjWRlu1EUsYxq3RIsZCpYUBmC4XvqKXJhhOnB/UONA2jFNIOr6p03pELW
aRyqfbT4s5xYm0p+uN43eQSJtjdiZv1shuPIYdvFuenffjhQqjoRDZBwGVjNSCYg
mKLfxDT6a0pTWWW7Y3bZ4SLUDkrL9YjMX22pExZJvrzj287ZW8WnQifO2VZqwaaD
I508DomhnCzjiilY40MXtj4rwQNLJyMa0xjBpvvfWb8hMikqN52ZOP8iF/CyeEP0
N6kslt+Qny3yCCQrs+uqNLoxqavzst8YwdhOky5t6NvKWI5VP2sZ4JJmF2xLL46N
nlZUya0CgYEA9mHggDymSNB07LqGHJZx3dsBC9fzgidFHClDWSc3mM7aj+kTKp2j
XRF2vWQHWYW1Dzh57pTmIqOJ0xs+PiROHT+6OZ6kEKNqCBfgeHPdXaz5krWcM/cx
Sw/FkWCOc+WQdOMQQroeSKwHuxFZt2AzzT4tU4j8hKmcBXuU3LkjwTcCgYEAyhXe
y0EevmFwHyeIn6C7MWXEoi0PjR1e9LN6X67XuI447aplovc8yY7hTNzpKRhlPEZ6
NfeAAAkjPHPTNQumsjY7iznsMGGpbN1ToguYTRYKvmbuCteuyBhpAdenuVgh/w2O
4uuIYeQlcBRfiuxJplRy3txtRXsU2u7tJvjtw8MCgYEAoHmzvhLCw95yqdX7kBc1
ZylEDzDC/F0TmHoP0bvHbJIerWlEAJfYVcAQNN84IkkCWz2PvaPiGWGnXYb7DYKc
FlTxuKHpfqTRZSAYJpxg7KjDjZkYeohg5OEK79uSLU6yvk8+whdzriXOizuL0fKp
Ct+aqjQpNUc7xh5uIS29ahUCgYAcOs/jrtYfnDbwczJXsjlUHjZIvWi1usuf/U5z
/VWvN1bmhG4sRMNeGLKKbTW5AuppcCL0VP2xg5VDhZ6Ug2sm7AKHYXEIFSx4w7ZC
JcKByjl3/aL1KsoEs7w/gKOydYhSO8+hDWwA2MEOFhp+qqFjNdrSHRK6qQXxy3yf
fBiixwKBgQC5qtZL5U0czjuAlXKWbt+C8n4PzsIm4dRjiooQ/oAM8SrsqTyOCsLC
WVuqUiFpdxED8fb25SmHI7I6h6PpO8Meuhe2OSSZL+Io8sayvTzllXIK9Vid1ySx
RR5aSIWng9h8oqqjmaNhEeVI61Mlc1wfdwLIiEAeZTAVMFOqF7MDeA==
-----END RSA PRIVATE KEY-----
[root@centos79-base01 ~]# ssh-copy-id root@192.168.1.11
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.1.11's password: #输入远程用户的密码
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.1.11'"
and check to make sure that only the key(s) you wanted were added.
[root@centos79-base02 ~]# ll .ssh/
total 8
-rw------- 1 root root 402 Nov 13 17:45 authorized_keys
-rw-r--r-- 1 root root 174 Nov 13 16:35 known_hosts
[root@centos79-base02 ~]# cat .ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDCfkeZGVjaFApoRP2tFcFSAnkXRGJGY9lYqUrVLmy8htlCn/BLuK7T4gLCHRkDqWKmeVRP94D3A2fe+dzO3OT9pNqpUdtNp6tEQcTArUEy4IIVIufO41dfLgYVNR2d3T1Yd9Yy4PAJSJItbHlWGfAkr7iCVsp6EDsbMKuFe+uhYrDzSIG75adfjCz+bJBtbHimVIWrnQ5819z2+CV70hqooNPBnBM2z6/UNoObA/pRxZ4g9huS8GuuYen5Gif0nB5jW+msOaTDEXXgjndf0AIr1FoXbcEEi9YnZW78YFSGNWausoe+SM6C0S75unn/BDLhTsQUSHhc3/+JJ5hqVBHl root@centos79-base01
[root@centos79-base01 ~]# ssh 192.168.1.11
Last login: Sun Nov 13 17:31:06 2022 from 192.168.1.1
[root@centos79-base02 ~]# hostname -I
192.168.1.11
[root@centos79-base01 ~]# scp /data/index.html 192.168.1.11:/root/
index.html 100% 6 5.8KB/s 00:00
[root@centos79-base02 ~]# ll
total 8
-rw-------. 1 root root 1447 Nov 8 14:53 anaconda-ks.cfg
-rwxr-xr-x 1 root root 6 Nov 13 17:49 index.html# 利用expect实现ssh key的批量部署
#!/bin/bash
COLOR="echo -e \E[1;32m"
END="\E[0m"
PASSWORD=root123
IPLIST="
192.168.1.10
192.168.1.11
"
[ ! -f ~/.ssh/id_rsa ] && ssh-keygen -P "" -f ~/.ssh/id_rsa &>/dev/null
rpm -q expect &> /dev/null || yum -y -q install expect &>/dev/null
for ip in $IPLIST ;do
{
expect <<EOF
set timeout 60
spawn ssh-copy-id $ip
expect {
"yes/no" { send "yes\r";exp_continue }
"password:" { send "$PASSWORD\r" }
}
expect eof
EOF
$COLOR"$ip is ready"$END
}&
done
wait
$COLOR"Push ssh key is finished!"$END
#!/bin/bash
PASS=magedu
rpm -q expect &> /dev/null || yum -y install expect &> /dev/null
if [ ! -e /root/.ssh/id_rsa ];then
ssh-keygen -t rsa -P "" -f /root/.ssh/id_rsa &> /dev/null
echo "ssh key is created"
fi
while read IP ;do
expect &> /dev/null <<EOF #或者expect <<EOF &> /dev/null
set timeout 20
spawn ssh-copy-id -i /root/.ssh/id_rsa.pub root@$IP
expect {
"yes/no" { send "yes\n";exp_continue }
"password" { send "$PASS\n" }
}
expect eof
EOF
echo $IP is ready
done < hosts.txt
2.5、ssh服务器配置
- 服务器端:sshd
- 服务器端的配置文件: /etc/ssh/sshd_config
- 服务器端的配置文件帮助:man 5 sshd_config
# 常用参数
Port 22 #生产环境建议修改
ListenAddress ip
LoginGraceTime 2m
PermitRootLogin yes #默认ubuntu不允许root远程ssh登录
StrictModes yes #检查.ssh/文件的所有者,权限等
MaxAuthTries 6 #最大认证次数
MaxSessions 10 #同一个连接最大会话
PubkeyAuthentication yes #基于key验证
PermitEmptyPasswords no #空密码连接
PasswordAuthentication yes #基于用户名和密码连接
GatewayPorts no
ClientAliveInterval 10 #单位:秒
ClientAliveCountMax 3 #默认3
UseDNS yes #提高速度可改为no
GSSAPIAuthentication yes #提高速度可改为no
MaxStartups #未认证连接最大值,默认值10
Banner /path/file
# 以下可以限制可登录用户的办法:
AllowUsers user1 user2 user3
DenyUsers user1 user2 user3
AllowGroups g1 g2
DenyGroups g1 g2# 设置 ssh 空闲60s 自动注销
Vim /etc/ssh/sshd_config
ClientAliveInterval 60
ClientAliveCountMax 0
# 解决ssh登录缓慢的问题
vim /etc/ssh/sshd_config
UseDNS no
GSSAPIAuthentication no
# 在 ubuntu 上启用 root 远程ssh登录
vim /etc/ssh/sshd_config
PermitRootLogin yesssh 服务的最佳实践
- 建议使用非默认端口
- 禁止使用protocol version 1
- 限制可登录用户
- 设定空闲会话超时时长
- 利用防火墙设置ssh访问策略
- 仅监听特定的IP地址
- 基于口令认证时,使用强密码策略,比如:tr -dc A-Za-z0-9_ < /dev/urandom | head -c 12|xargs
- 使用基于密钥的认证
- 禁止使用空密码
- 禁止root用户直接登录
- 限制ssh的访问频度和并发在线数
- 经常分析日志
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END