8、网络防火墙
iptables/netfilter 利用filter表的FORWARD链,可以充当网络防火墙
- 请求-响应报文均会经由FORWARD链,要注意规则的方向性
- 如果要启用conntrack机制,建议将双方向的状态为ESTABLISHED的报文直接放行
8.1、FORWARD 链实现内外网络的流量控制
范例:实现内网访问可以访问外网,反之禁止
![图片[1]-iptables(下)-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/FORWARD-2.jpg)
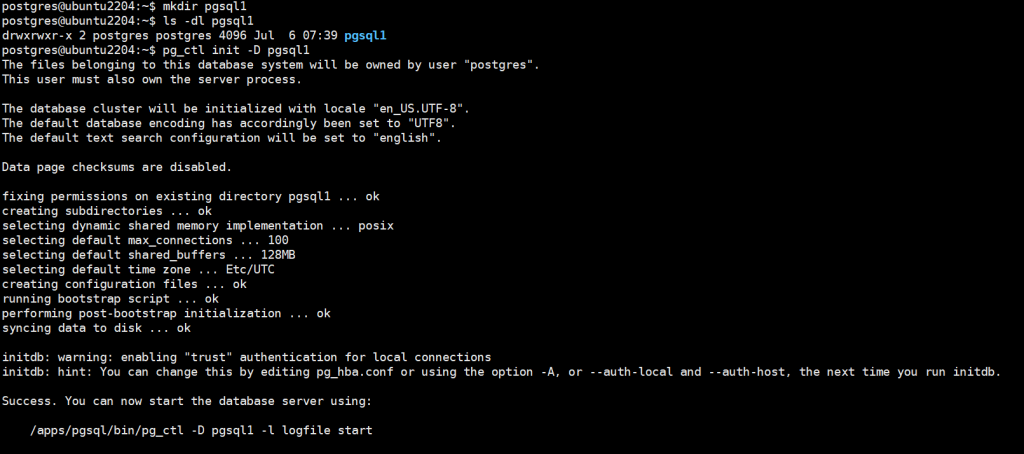
# 环境准备
# 修改各服务器IP
[root@internet ~]# hostname -I
192.168.2.10
[root@fw ~]# hostname -I
192.168.1.11 192.168.2.11
[root@neiwang01 ~]# hostname -I
192.168.1.12
[root@neiwang02 ~]# hostname -I
192.168.1.13
#查看各服务器路由
[root@internet ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.2.11 0.0.0.0 UG 100 0 0 eth0
192.168.2.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
[root@fw ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.1.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
192.168.2.0 0.0.0.0 255.255.255.0 U 101 0 0 eth1
[root@neiwang01 ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.1.11 0.0.0.0 UG 100 0 0 eth0
192.168.1.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
[root@neiwang02 ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.1.11 0.0.0.0 UG 100 0 0 eth0
192.168.1.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
# FW配置内核参数允许转发
[root@fw ~]# vim /etc/sysctl.conf
net.ipv4.ip_forward=1
[root@fw ~]# sysctl -p
net.ipv4.ip_forward = 1
# 目前内网可以访问外网资源
[root@neiwang01 ~]# ping 192.168.2.10
PING 192.168.2.10 (192.168.2.10) 56(84) bytes of data.
64 bytes from 192.168.2.10: icmp_seq=1 ttl=63 time=8.31 ms
64 bytes from 192.168.2.10: icmp_seq=2 ttl=63 time=1.52 ms
^C
--- 192.168.2.10 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 1.522/4.919/8.316/3.397 ms
[root@neiwang01 ~]# curl http://192.168.2.10
hello
[root@neiwang02 ~]# ping 192.168.2.10
PING 192.168.2.10 (192.168.2.10) 56(84) bytes of data.
64 bytes from 192.168.2.10: icmp_seq=1 ttl=63 time=0.622 ms
64 bytes from 192.168.2.10: icmp_seq=2 ttl=63 time=0.900 ms
^C
--- 192.168.2.10 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 0.622/0.761/0.900/0.139 ms
[root@neiwang02 ~]# curl http://192.168.2.10
hello# 通过标准模块实现内网访问外网特定服务http或icmp,反之禁止
# 配置命令
[root@fw ~]# iptables -A FORWARD -j REJECT
# 效果
[root@neiwang01 ~]# ping 192.168.2.10
PING 192.168.2.10 (192.168.2.10) 56(84) bytes of data.
From 192.168.1.11 icmp_seq=1 Destination Port Unreachable
From 192.168.1.11 icmp_seq=2 Destination Port Unreachable
^C
--- 192.168.2.10 ping statistics ---
2 packets transmitted, 0 received, +2 errors, 100% packet loss, time 1000ms
[root@neiwang01 ~]# curl http://192.168.2.10
curl: (7) Failed connect to 192.168.2.10:80; Connection refused
# 配置命令
[root@fw ~]# iptables -I FORWARD -s 192.168.1.0/24 -p tcp --dport 80 -j ACCEPT
[root@fw ~]# iptables -I FORWARD -d 192.168.1.0/24 -p tcp --sport 80 -j ACCEPT
# 效果
[root@neiwang01 ~]# curl http://192.168.2.10
hello
[root@neiwang02 ~]# curl http://192.168.2.10
hello
# 配置命令
[root@fw ~]# iptables -I FORWARD -s 192.168.1.0/24 -p icmp --icmp-type 8 -j ACCEPT
[root@fw ~]# iptables -I FORWARD -d 192.168.1.0/24 -p icmp --icmp-type 0 -j ACCEPT
# 效果
[root@neiwang01 ~]# ping 192.168.2.10
PING 192.168.2.10 (192.168.2.10) 56(84) bytes of data.
64 bytes from 192.168.2.10: icmp_seq=1 ttl=63 time=0.519 ms
64 bytes from 192.168.2.10: icmp_seq=2 ttl=63 time=0.463 ms
^C
--- 192.168.2.10 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 0.463/0.491/0.519/0.028 ms
[root@neiwang02 ~]# ping 192.168.2.10
PING 192.168.2.10 (192.168.2.10) 56(84) bytes of data.
64 bytes from 192.168.2.10: icmp_seq=1 ttl=63 time=0.431 ms
^C
--- 192.168.2.10 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.431/0.431/0.431/0.000 ms
# 查看iptables配置
[root@fw ~]# iptables -vnL
![图片[2]-iptables(下)-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-98.png)
8.2、NAT 表
NAT: network address translation,支持PREROUTING,INPUT,OUTPUT,POSTROUTING四个链
请求报文:修改源/目标IP,由定义如何修改
响应报文:修改源/目标IP,根据跟踪机制自动实现
NAT的实现分为下面类型:
- SNAT:source NAT ,支持POSTROUTING, INPUT,让本地网络中的主机通过某一特定地址访问外部网络,实现地址伪装,请求报文:修改源IP
- DNAT:destination NAT 支持PREROUTING , OUTPUT,把本地网络中的主机上的某服务开放给外部网络访问(发布服务和端口映射),但隐藏真实IP,请求报文:修改目标IP
- PNAT: port nat,端口和IP都进行修改
8.3、SNAT
SNAT:基于nat表的target,适用于固定的公网IP
iptables -t nat -A POSTROUTING -s LocalNET ! -d LocalNet -j SNAT --to-source ExtIP
--to-source [ipaddr[-ipaddr]][:port[-port]]
--random
# 需要开启 ip_forwardMASQUERADE:基于nat表的target,适用于动态的公网IP,如:拨号网络
iptables -t nat -A POSTROUTING -s LocalNET ! -d LocalNet -j MASQUERADE
--to-ports port[-port]
--random范例:SNAT
![图片[3]-iptables(下)-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/NAT-1.jpg)
# FW配置内核参数允许转发
[root@fw ~]# vim /etc/sysctl.conf
net.ipv4.ip_forward=1
[root@fw ~]# sysctl -p
net.ipv4.ip_forward = 1# 针对专线静态公共IP
[root@fw ~]# iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -j SNAT --to-source 192.168.2.11
# 针对拨号网络和专线静态公共IP
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -j MASQUERADE
# 效果
[root@neiwang01 ~]# ping 192.168.2.10
PING 192.168.2.10 (192.168.2.10) 56(84) bytes of data.
64 bytes from 192.168.2.10: icmp_seq=1 ttl=63 time=0.356 ms
64 bytes from 192.168.2.10: icmp_seq=2 ttl=63 time=2.32 ms
64 bytes from 192.168.2.10: icmp_seq=3 ttl=63 time=0.547 ms
64 bytes from 192.168.2.10: icmp_seq=4 ttl=63 time=1.98 ms
64 bytes from 192.168.2.10: icmp_seq=5 ttl=63 time=0.351 ms
64 bytes from 192.168.2.10: icmp_seq=6 ttl=63 time=0.428 ms
64 bytes from 192.168.2.10: icmp_seq=7 ttl=63 time=0.378 ms
^C
--- 192.168.2.10 ping statistics ---
7 packets transmitted, 7 received, 0% packet loss, time 6004ms
rtt min/avg/max/mdev = 0.351/0.909/2.322/0.795 ms
[root@neiwang01 ~]# curl http://192.168.2.10
hello
# 查看转换状态信息
[root@fw ~]# cat /proc/net/nf_conntrack
ipv4 2 tcp 6 66 TIME_WAIT src=192.168.1.13 dst=192.168.2.10 sport=41926 dport=80 src=192.168.2.10 dst=192.168.2.11 sport=80 dport=41926 [ASSURED] mark=0 zone=0 use=2
ipv4 2 tcp 6 38 TIME_WAIT src=192.168.1.12 dst=192.168.2.10 sport=45956 dport=80 src=192.168.2.10 dst=192.168.2.11 sport=80 dport=45956 [ASSURED] mark=0 zone=0 use=2
# 在外网服务器查看到是firewalld的地址在访问
# 查看iptables规则![图片[4]-iptables(下)-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-99.png)
![图片[5]-iptables(下)-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-100.png)
8.4、DNAT
DNAT:nat表的target,适用于端口映射,即可重定向到本机,也可以支持重定向至不同主机的不同端口,但不支持多目标,即不支持负载均衡功能
iptables -t nat -A PREROUTING -d ExtIP -p tcp|udp --dport PORT -j DNAT --to-destination InterSeverIP[:PORT]
--to-destination [ipaddr[-ipaddr]][:port[-port]]
# 需要开启 ip_forward
范例:DNAT
![图片[1]-iptables(下)-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/FORWARD-2.jpg)
# FW配置内核参数允许转发
[root@fw ~]# vim /etc/sysctl.conf
net.ipv4.ip_forward=1
[root@fw ~]# sysctl -p
net.ipv4.ip_forward = 1# 将外网端口转换成内网地址给内网访问
[root@fw ~]# iptables -t nat -A PREROUTING -d 192.168.1.11 -p tcp --dport 80 -j DNAT --to-destination 192.168.2.10:80
[root@fw ~]# iptables -vnL -t nat![图片[7]-iptables(下)-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-101.png)
# 内网验证
[root@neiwang01 ~]# curl http://192.168.1.11:80
hello
[root@neiwang02 ~]# curl http://192.168.1.11:80
hello© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END