OpenVPN的管理功能主要关于安全加强及客户端的证书管理,用户密码验证等
1、启用安全增强功能
# 启用防止DoS攻击的安全增强配置
openvpn --genkey --secret /etc/openvpn/certs/ta.key
ll /etc/openvpn/certs
total 24
-rw------- 1 root root 1204 Aug 3 20:34 ca.crt
-rw------- 1 root root 424 Aug 3 20:35 dh.pem
-rw------- 1 root root 4608 Aug 3 20:34 server.crt
-rw------- 1 root root 1704 Aug 3 20:35 server.key
-rw------- 1 root root 636 Aug 4 15:53 ta.key
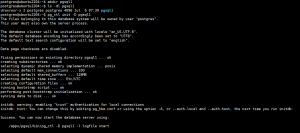
vim /etc/openvpn/server.conf
tls-auth /etc/openvpn/certs/ta.key 0 #客户端为1,服务器端为0
systemctl restart openvpn@server.service
将ta.key 传到客户端相关目录下
![图片[1]-OpenVPN 管理-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-152.png)
修改客户端配置文件clent.ovpn,添加一行
tls-auth ta.key 1 #客户端为1,服务器端为02、设置客户端的私钥密码增强安全性
新建一个账户test,并且设置证书密码,提高证书及登录VPN的安全性。
# 创建新用户,生成对应的有密码的私钥和证书申请
pwd
/etc/openvpn/easy-rsa-client/3
./easyrsa gen-req test
Enter PEM pass phrase:
#输入两遍密码
Verifying - Enter PEM pass phrase:
#输入两遍密码# 导入用户证书申请并颁发证书
pwd
/etc/openvpn/easy-rsa-server/3
./easyrsa import-req /etc/openvpn/easy-rsa-client/3/pki/reqs/test.req test
# 确保证书有效期是合理值
grep EASYRSA_CERT_EXPIRE vars
set_var EASYRSA_CERT_EXPIRE 90
# 颁发证书
./easyrsa sign client test# 将用户的证书相关文件放在指定的目录中
mkdir /etc/openvpn/client/test
cp /etc/openvpn/easy-rsa-server/3/pki/issued/test.crt /etc/openvpn/client/test/
cp /etc/openvpn/easy-rsa-client/3/pki/private/test.key /etc/openvpn/client/test/
cp /etc/openvpn/certs/{ca.crt,ta.key} /etc/openvpn/client/test/
cp /etc/openvpn/client/lijiacheng/client.ovpn /etc/openvpn/client/test/# 根据服务器端修改下面配置,需要和服务器同步
cat client.ovpn
client
dev tun
proto tcp
remote 10.0.0.8 1194
resolv-retry infinite
nobind
#persist-key
#persist-tun
ca ca.crt
cert magedu.crt
key magedu.key
remote-cert-tls server
tls-auth ta.key 1
cipher AES-256-CBC
verb 3
compress lz4-v2
a将/etc/openvpn/client/test目录下文件放置到windows客户端的 C:\Program Files\OpenVPN\config 目录下
客户端重新连接
![图片[2]-OpenVPN 管理-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-153.png)
3、账户证书管理
对新员工的入职和老员工的离职,会涉及到证书的创建和吊销
# 证书自动过期
# 前面颁发的证书都有有一定的有效期,过期后就需要重新颁发新证书
# 过期时间由以下设置决定
grep EASYRSA_CERT_EXPIRE /etc/openvpn/easy-rsa-server/3/vars
set_var EASYRSA_CERT_EXPIRE 90
# 如果证书过期,在服务器端可以看到以下日志
# 让服务器时间改为2年后时间
date -s '2 year'
# 服务器端日志中会显示用户证书过期
tail -n0 /var/log/openvpn/openvpn.log -f
Thu Aug 4 17:42:22 2022 TCP connection established with [AF_INET]10.0.0.1:11324
Thu Aug 4 17:42:23 2022 10.0.0.1:11324 TLS: Initial packet from
[AF_INET]10.0.0.1:11324, sid=a2957674 874cf1f7
Thu Aug 4 17:42:24 2022 10.0.0.1:11324 VERIFY OK: depth=1, CN=Easy-RSA CA
Thu Aug 4 17:42:24 2022 10.0.0.1:11324 VERIFY ERROR: depth=0, error=certificate
has expired: CN=test
Thu Aug 4 17:42:24 2022 10.0.0.1:11324 OpenSSL: error:1417C086:SSL
routines:tls_process_client_certificate:certificate verify failed
Thu Aug 4 17:42:24 2022 10.0.0.1:11324 TLS_ERROR: BIO read tls_read_plaintext
error
Thu Aug 4 17:42:24 2022 10.0.0.1:11324 TLS Error: TLS object -> incoming
plaintext read error
Thu Aug 4 17:42:24 2022 10.0.0.1:11324 TLS Error: TLS handshake failed
Thu Aug 4 17:42:24 2022 10.0.0.1:11324 Fatal TLS error (check_tls_errors_co),
restarting
Thu Aug 4 17:42:24 2022 10.0.0.1:11324 SIGUSR1[soft,tls-error] received,
client-instance restarting
# 证书手动注销
# 查看当前证书的有效性
# 证书有效为V,无效为R
cat /etc/openvpn/easy-rsa-server/3/pki/index.txt
V 201031091943Z EDAEBAB8D65066D307AE58ADC1A56682 unknown /CN=server
V 201031153815Z 5FE114ACC4FE6AB89D17E1B0EECF2B78 unknown
/CN=lijiacheng
V 201102083043Z C971227DA77824C8ACB7D655D09D4081 unknown /CN=test
# 吊销指定的用户的证书
cd /etc/openvpn/easy-rsa-server/3
./easyrsa revoke test
# 查看当前证书的有效性,有效为V,无效为R
cat /etc/openvpn/easy-rsa-server/3/pki/index.txt
V 201031091943Z EDAEBAB8D65066D307AE58ADC1A56682 unknown /CN=server
V 201031153815Z 5FE114ACC4FE6AB89D17E1B0EECF2B78 unknown
/CN=lijiacheng
R 201102083043Z 200805123127Z C971227DA77824C8ACB7D655D09D4081 unknown
/CN=test
# 当前断开客户端连接,magedu用户仍然能连接成功# 每次吊销证书后都需要更新证书吊销列表文件,并且需要重启OpenVPN服务
./easyrsa gen-crl
# 传到windows上,修改文件后缀为crl,双击就可以打开此文件,看到下面显示信息
cat pki/crl.pem
![图片[3]-OpenVPN 管理-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-154.png)
# 将吊销列表文件发布
# 第一次吊销证时需要编辑配置文件调用吊销证书的文件,后续吊销无需此步
vim /etc/openvpn/server.conf
crl-verify /etc/openvpn/easy-rsa-server/3/pki/crl.pem
# 每次吊销证书后,都需要重新启动才能生效
systemctl restart openvpn@server.service
# 账户重名证书颁发
# 对于员工重名的情况,可以为新员工指定新的名称,或者删除不再使用的重名用户证书,重新创建新证书
# 删除已被吊销的账户证书
cd /etc/openvpn/easy-rsa-client/3/
rm -f pki/private/test.key
rm -f pki/reqs/test.req
rm -rf /etc/openvpn/client/test/*
rm -f /etc/openvpn/easy-rsa-server/3/pki/reqs/test.req
rm -f /etc/openvpn/easy-rsa-server/3/pki/issued/test.crt
#删除之前的带R的吊销记录
[root@centos8 3]#vim /etc/openvpn/easy-rsa-server/3/pki/index.txt# 自动化的证书颁发脚本
[root@openvpn ~]# vim openvpn-user-crt.sh
#!/bin/bash
. /etc/init.d/functions
OPENVPN_SERVER=192.168.1.30
PASS=123456
remove_cert () {
rm -rf /etc/openvpn/client/${NAME}
find /etc/openvpn/ -name "$NAME.*" -delete
}
create_cert () {
cd /etc/openvpn/easy-rsa-client/3
./easyrsa gen-req ${NAME} nopass <<EOF
EOF
cd /etc/openvpn/easy-rsa-server/3
./easyrsa import-req /etc/openvpn/easy-rsa-client/3/pki/reqs/${NAME}.req ${NAME}
./easyrsa sign client ${NAME} <<EOF
yes
EOF
mkdir /etc/openvpn/client/${NAME}
cp /etc/openvpn/easy-rsa-server/3/pki/issued/${NAME}.crt /etc/openvpn/client/${NAME}
cp /etc/openvpn/easy-rsa-client/3/pki/private/${NAME}.key /etc/openvpn/client/${NAME}
cp /etc/openvpn/certs/{ca.crt,ta.key} /etc/openvpn/client/${NAME}
cat > /etc/openvpn/client/${NAME}/client.ovpn <<EOF
client
dev tun
proto tcp
remote ${OPENVPN_SERVER} 1194
resolv-retry infinite
nobind
#persist-key
#persist-tun
ca ca.crt
cert $NAME.crt
key $NAME.key
remote-cert-tls server
tls-auth ta.key 1
cipher AES-256-CBC
verb 3
compress lz4-v2
EOF
echo "证书存放路径:/etc/openvpn/client/${NAME},证书文件如下:"
echo -e
"\E[1;32m******************************************************************\E[0m"
ls -l /etc/openvpn/client/${NAME}
echo -e
"\E[1;32m******************************************************************\E[0m"
cd /etc/openvpn/client/${NAME}
zip -qP "$PASS" /root/${NAME}.zip *
action "证书的打包文件已生成: /root/${NAME}.zip"
}
read -p "请输入用户的姓名拼音(如:lijiacheng): " NAME
remove_cert
create_cert
# 执行脚本
[root@openvpn ~]# bash openvpn-user-crt.sh
请输入用户的姓名拼音(如:lijiacheng): test
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-client/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
......................................+++
...............+++
writing new private key to '/etc/openvpn/easy-rsa-client/3/pki/easy-rsa-28787.yaA55D/tmp.FUihQF'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [test]:
Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa-client/3/pki/reqs/test.req
key: /etc/openvpn/easy-rsa-client/3/pki/private/test.key
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
The request has been successfully imported with a short name of: test
You may now use this name to perform signing operations on this request.
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.
Request subject, to be signed as a client certificate for 90 days:
subject=
commonName = test
Type the word 'yes' to continue, or any other input to abort.
Confirm request details: Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-28835.xMTW3F/tmp.D3YNw2
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'test'
Certificate is to be certified until Feb 20 05:14:39 2023 GMT (90 days)
Write out database with 1 new entries
Data Base Updated
Certificate created at: /etc/openvpn/easy-rsa-server/3/pki/issued/test.crt
cp: cannot stat ‘/etc/openvpn/certs/ta.key’: No such file or directory
证书存放路径:/etc/openvpn/client/test,证书文件如下:
openvpn-user-crt.sh: line 48: \E[1;32m******************************************************************\E[0m: command not found
total 20
-rw------- 1 root root 1176 Nov 22 13:14 ca.crt
-rw-r--r-- 1 root root 225 Nov 22 13:14 client.ovpn
-rw------- 1 root root 4430 Nov 22 13:14 test.crt
-rw------- 1 root root 1704 Nov 22 13:14 test.key
openvpn-user-crt.sh: line 51: \E[1;32m******************************************************************\E[0m: command not found
证书的打包文件已生成: /root/test.zip [ OK ]
4、实现用户密码认证
基于证书验证的基础上再加上用户名密码验证可以实现更高的安全性
# 修改服务端配置
vim /etc/openvpn/server.conf
# 添加三行,实现服务端支持密码认证方式
script-security 3 # 允许使用自定义脚本
auth-user-pass-verify /etc/openvpn/checkpsw.sh via-env #指定自定义脚本路径
username-as-common-name #开启用户密码验证
# 创建自定义脚本
# 官方脚本下载 http://openvpn.se/files/other/checkpsw.sh
[root@openvpn ~]# vim /etc/openvpn/checkpsw.sh
#!/bin/sh
PASSFILE="/etc/openvpn/psw-file"
LOG_FILE="/var/log/openvpn-password.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
if [ ! -r "${PASSFILE}" ]; then
echo "${TIME_STAMP}: Could not open password file \"${PASSFILE}\" for reading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk '!/^;/&&!/^#/&&$1=="'${username}'"{print $2;exit}' ${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = "" ]; then
echo "${TIME_STAMP}: User does not exist: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
echo "${TIME_STAMP}: Successful authentication: username=\"${username}\".">> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
# 增加执行权限
chmod +x /etc/openvpn/checkpsw.sh
# 创建用户密码文件,每行是一个用户和密码
cat > /etc/openvpn/psw-file <<EOF
test 123456
test2 654321
EOF
systemctl restart openvpn@server
# 修改客户端配置
vim /etc/openvpn/client/lijiacheng/client.ovpn
#加下面一行,可以支持用户密码认证
auth-user-pass
![图片[4]-OpenVPN 管理-李佳程的个人主页](http://www.lijiach.com/wp-content/uploads/2022/11/image-155.png)
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END